How to complete a Device Audit with RoboShadow
One of the most common failures we see within a good Internal Penetration Test will be devices that are not monitored correctly from a Cyber Perspective. In particular, it's the devices you don't know you have that access business data which is where the penetration testers and bad actors like to pick up on. Regardless of how you achieve it, you should ensure you have the data to know where all your devices are, and what their Cyber compliance capabilities are.
The first thing an internal Penetration tester will do is get a list of machines from a Primary User Store (like Active Directory, Azure AD, or Google Workspaces) and proceed to try and find the feral machines. Being able to reconcile your own estate with a primary user store to know you have covered the basics is a must for any IT management / cyber team.
Our RoboShadow platform aims to make it easy to perform a Device Audit from a single console, allowing you to consolidate against your Primary User Store.
How to Perform A Device Audit with RoboShadow
After you have installed the RoboShadow agent to your users, you reconcile agentless machines in two ways. You can either using Azure AD or using On Premise AD. Preferably you should use Azure Active Directory, but this may not catch any non Azure AD joined machines. If you have any doubt that not all of your machines and servers are in Azure then please also complete step 2. (Step 2 may require you to involve your IT department).
Step 1: Roll out the roboShadow agent to your users
You will firstly need to ensure that the RoboShadow agent is installed on all your devices. You can roll out the Agent to your users using a GPO or other method suggested by your IT department.
Step 2: Connect your Azure Active Directory
1. Within the RoboShadow Portal, select 'Cloud' then 'Azure/365 MFA'.
2. Setup your Active Directory Synchronisation by selecting 'Configure AD Sync'.
Please note: You will need to have a Global Administrator account, as well as an Azure Active Directory Premium P2 license assigned to your Microsoft tenancy in order to complete this step.

3. Sign in to your global administrator account within the 365 portal.
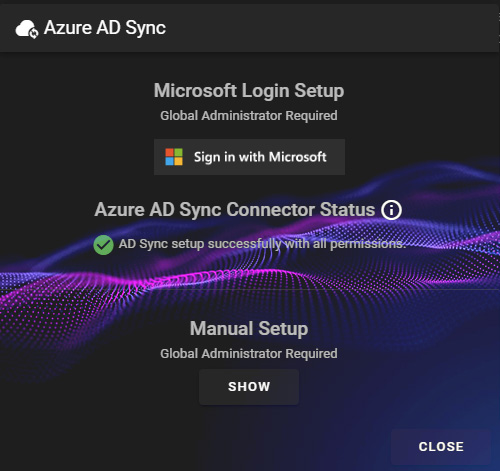
4. You will now see a list of permissions that RoboShadow will need access to, click on 'Accept' if you are happy to proceed.

5. You will see a screen where it is syncing your AD. When this is complete, you will be able to select 'Return to Dashboard'.
Step Three: Connect your On-Premise Active Directory
As this step has several steps, please follow the guide within the RoboShadow Help Page to sync your users.
Once these steps are completed, you will be able to confirm that both your On-Premise and Azure AD Syncs have been completed successfully by going to the Device Synchronisation Page and checking your synchronisation status.
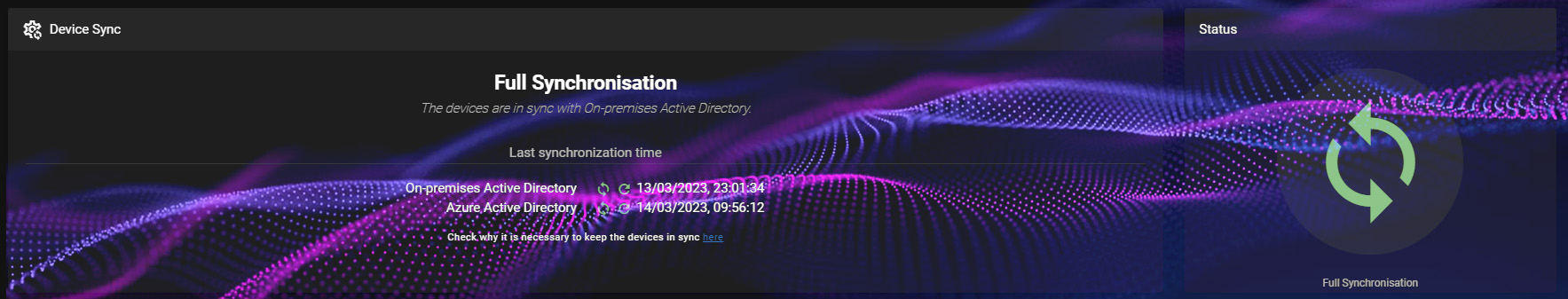
Step Four: Filter your report to find agentless machines
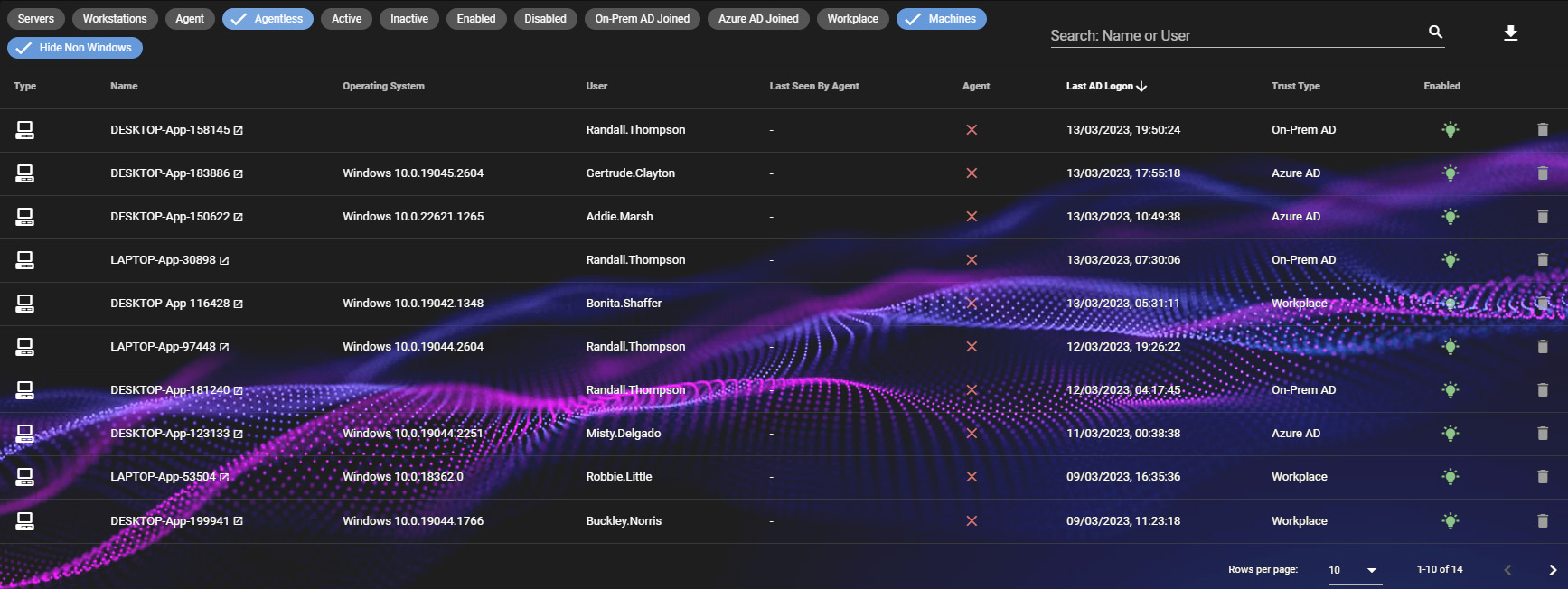
On the Device Synchronisation Page you will now see a list of all of your connected devices and users, with several options to filter them.
Select the 'Agentless Machines' filter to see a list of machines and users who do not have the RoboShadow agent installed which may be outside of your known network.
Further Information about Device Audits.
Why is it important to audit the devices connected to your Azure or On Prem Active Directory?
By auditing the devices connected to your Azure or On Prem Active Directory, you can gain insight into who has access to your resources and what applications they are using. This helps you maintain a secure environment by ensuring that only authorized users have access. It also helps identify any security threats as soon as possible and take action to prevent them from causing damage. Additionally, auditing helps you keep track of changes to user accounts and devices which can help reduce the risk of malicious activity. Finally, regular audits allow you to identify any areas where your security protocols may need improvement or updating. Auditing is an important part of keeping your IT environment secure and ensuring compliance with industry regulations.
Why are unmonitored devices a common penetration test failure?
Unmonitored devices can be a common failure point during penetration tests because they are not regularly reviewed and audited. This means that any malicious activities or security vulnerabilities are often overlooked. Unmonitored devices also increase the attack surface, making it easier for adversaries to gain access to sensitive data or resources. Additionally, unmonitored devices may have outdated or vulnerable software installed or outdated security configurations, making them prime targets for attackers. It is important to regularly audit and monitor all devices connected to your Azure or On Prem Active Directory in order to reduce the risk of a successful attack.
What are some best practices for auditing devices connected to your Azure or On Prem Active Directory?
- Using automated tools to scan and detect any unauthorized access attempts, such as suspicious logins or changes in user accounts.
- Regularly reviewing logs to identify any malware programs or malicious activity.
- Setting up alerts to notify you of any suspicious activity or unauthorized access attempts.
- Running vulnerability scans and patching devices to ensure they are running the most up-to-date versions of software and security protocols.
- Requiring users to use two-factor authentication on high-risk systems.
Thank You!
We hope you found this blog useful. Did you know you can also use RoboShadow to audit another common penetration test failure? Check out our blog on How to Audit MFA Compliance with RoboShadow for more information.
I’m lucky to have worked in technology all over the world for large multi-national organisations, in recent years I have built technology brands and developed products to help make technology that bit easier for people to grasp and manage. By day I run tech businesses, by night (as soon as the kids have gone to bed) I write code and I love building Cyber Security technology.




