The year is flying past! Microsoft released September's Patch Tuesday update yesterday, releasing updates for 81 vulnerabilities, which includes 2 publicly disclosed zero days.
Pssst, as a reminder... did you know that you can now set up AutoFix rules for Windows Updates with RoboShadow's Cyber Heal function?
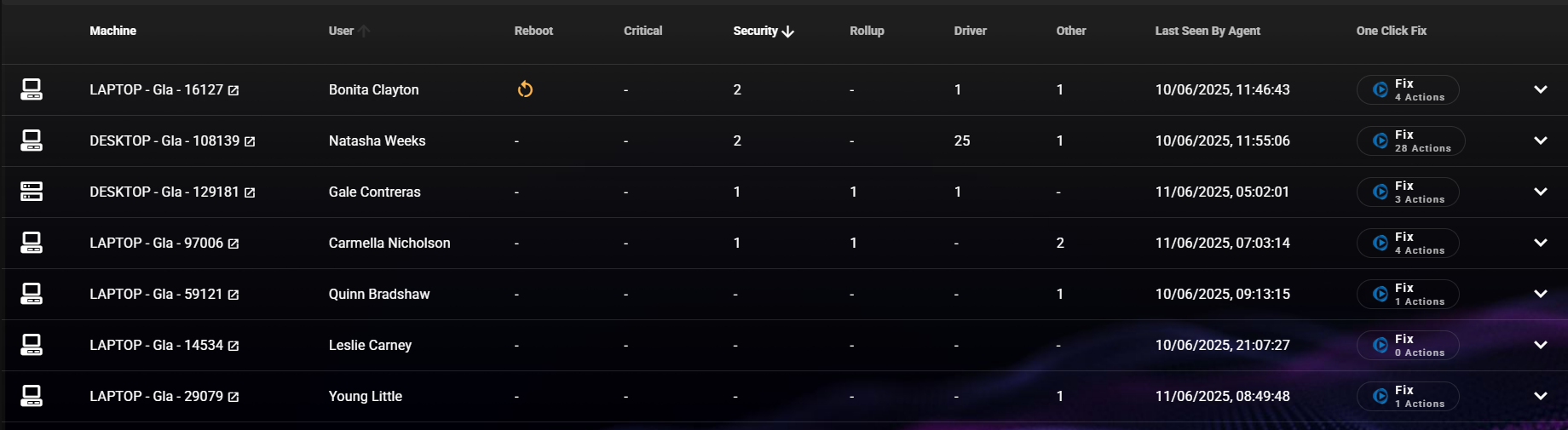
You can find a full list of security updates for September here.

Key Updates
- 81 Vulnerabilities Patched
- 2 publicly disclosed zero-day
- 9 critical vulnerabilities
Vulnerability Types Released in September 2025:
.png?width=516&height=387&name=output%20(8).png)
Zero Day Vulnerabilities
CVE-2025-55234 – Windows SMB Elevation of Privilege
- CVSS Score 8.8 (High)
- Description: This is an Elevation of Privilege (EoP) vulnerability in Windows Server Message Block (SMB) Server. The flaw stems from improper authentication—specifically, the SMB Server may be susceptible to relay attacks depending on its configuration. An attacker successfully exploiting this vulnerability could perform relay attacks and escalate privileges to that of a compromised user. Microsoft has introduced audit capabilities in the September 2025 security updates to help administrators evaluate their environments and identify compatibility issues before enforcing hardening measures such as SMB Server Signing and SMB Server Extended Protection for Authentication (EPA)
- Exploitation Status: Publicly disclosed zero-day; no known active exploitation, though proof-of-concept (PoC) code may exist. Administrators are encouraged to enable auditing and gradually enforce SMB signing and EPA to avoid breaking legacy systems
CVE-2024-21907 – Improper Handling of Exceptional Conditions in Newtonsoft.Json
- CVSS Score 8.8 (High)
- Description: Versions of Newtonsoft.Json prior to 13.0.1 suffer from improper handling of deep nesting in JSON. Passing crafted, deeply nested data to
JsonConvert.DeserializeObject may trigger a StackOverflowException, or cause excessive CPU and memory consumption—resulting in a Denial of Service (DoS). An unauthenticated, remote attacker could exploit this vulnerability depending on how the library is used.
- Exploitation Status: Publicly disclosed; proof-of-concept exploits exist. Mitigation is available via upgrading to version 13.0.1 or later, and/or by setting a
MaxDepth limit (e.g., MaxDepth = 128) to fail fast on overly nested JSON.
Critical Vulnerability Summary
The following critical CVEs have been remediated this month, and should be patched as soon as possible:
| CVE |
CVSS |
Description Summary |
| CVE-2025-54914 |
10 |
Azure Networking Elevation of Privilege Vulnerability. |
| CVE-2025-54918 |
8.8 |
Windows NTLM Elevation of Privilege Vulnerability (SYSTEM privileges). |
| CVE-2025-54910 |
8.4 |
Microsoft Office Remote Code Execution Vulnerability (heap overflow). |
| CVE-2025-53800 |
7.8 |
Windows Graphics Component Elevation of Privilege Vulnerability. |
| CVE-2025-55228 |
7.8 |
Windows Graphics Component Remote Code Execution Vulnerability (race condition). |
| CVE-2025-55224 |
7.8 |
Windows Hyper-V Remote Code Execution Vulnerability. |
| CVE-2025-55236 |
7.3 |
DirectX Graphics Kernel Remote Code Execution Vulnerability (race condition). |
| CVE-2025-55226 |
6.7 |
Graphics Kernel Remote Code Execution Vulnerability (race condition/local exploit). |
| CVE-2025-53799 |
5.5 |
Windows Imaging Component Information Disclosure Vulnerability (heap leak). |

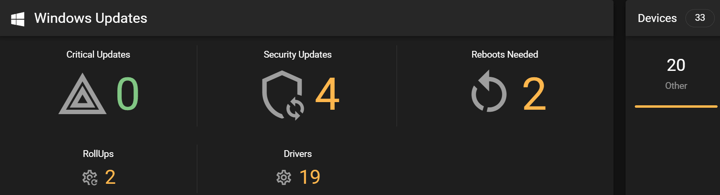
Actions to Take:
Here is what IT teams should prioritise this month:

If you have any questions about Patch Tuesday, or feedback on this blog please
reach out to us: hello@roboshadow.com
Thanks for reading!